Wireless Internet access points also called “hotspots” are increasingly available at cafes, malls and restaurants within business districts of Jakarta. The popularity of hotspots is increasing and more and more business people equip their laptops with wireless cards in order to have access to Internet while they are away of their desks. If you are a happy owner of a wireless enabled laptop, you can access your business e-mail, your on-line banking facility and your organization's network while enjoying your lunch meal at a restaurant. This certainly sounds exciting and user-friendly, yet are there any negative aspects of this new technology? This text presents results of my investigation in this area, plus explains how malicious hackers can access Internet on commercial hotspots, while real customers are paying for the connection.
Few weeks ago, a friend of mine told me about his problem related to use of a wireless hotspot service in Jakarta. As a happy owner of a laptop with wireless card, he started to use commercial wireless hotspot service provided by one of the local ISPs (Internet Service Providers) – unfortunately no free wireless is available at a mall near his office. The service is charged per minute and the price is within acceptable range if compared to ridiculously high fees charged by GPRS or CDMA service providers. Everything seemed to work fine for the first month, but then my friend noticed some irregularities in the use of the wireless hotspot service and the cost. So to speak, the cost of the service seemed to be double of what he thought he had actually used. Surprisingly, the ISP didn’t seem to be anyhow interested in this customer’s concern and simply answered “there is no problem with our service”, thus he asked me if I could help. Since the security of wireless communication has been within my interest for quite long, I decided to investigate.
Ground-Zero
For a preliminary testing ground we’ve chosen known mal in central Jakarta. The place got quite a few restaurants and cafes with commercial wireless hot-spot service available, plus there are many offices around and you can often see people using their laptops during lunch time.
At the day of testing, we are quipped with two IBM ThinkPad laptops using Windows XP Professional OS and with preinstalled tools used in this article. I realise most of you elite 31337 hackers would call me a total lamer for using Windows XP, so let me explain. To make it easier to understand the basis of wireless security and less likely to say “our systems are secure”, I decided use Windows XP. Additionally, I also want to show the simplicity of techniques presented here. Thus, if you are an advanced computer user or expert, please have in mind that this text is targeted to less experienced computer users.
Let's start
While seating at one of the cafés I fired-up my laptop and discovered several wireless networks available. Two of these hotspots were providing commercial wireless access service, among which one was often used by my friend. I connected to this wireless hotspot, ignored warnings displayed by Windows XP considering insecurity of the wireless network I am and simply tried to connect to
www.google.com.
As expected, an ISP web-site popped up with information that I need to log-in with my username and password in order to use the service. At the same time my friend using his laptop logged-in to the site and browsed through some web-sites.
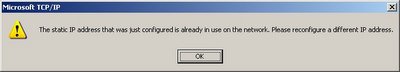
I disconnected from the wireless network and connected back several times, until this message box appeared on my screen:
Figure 1: IP Address Conflict Warning.
The same warning appeared on my friend’s laptop, and which was obvious conflict of the network IP address between our laptops. This was very surprising as the IP address was suppose to be automatically assigned by DHCP server and normally this should prevent from having two computers with same IP on the network. I ignored the message and tried to connect to
www.google.com. To my even greater surprise, I was successful connected – without any authentication to the ISP hotspot.
Meanwhile, my friend could not connect anywhere and disconnected from the network.
By simply connecting and disconnecting from the network I could get “free” access to Internet through commercial hotspot! Now the question was, if my friend was paying for this connection. I continued to use this Internet access for half an hour, checking my e-mail and reading news, after which we checked the status.
Clearly, I was using Internet on my friends account and he was not happy about it. Well, frankly he got MAD. He remembers seeing IP conflict warning several times, which could be the first clue explaining why he was paying more for the hotspot service that he should. Apparently, there was some bug in the hotspot application that allowed this thing to happen.
All very interesting, but we also wanted to know if this problem affects only this particular hotspot or also other hotspots of the same ISP. For this reason we moved to another mall in the central Jakarta – we got the list of hotspots from ISP web-site, thanks guys!
Initial analysis
The previously used approach tested on the other hotspot of the same ISP did not produce the same result. This indicates that DHCP issue might be only affecting only one hotspot. However, since we didn’t get the IP conflict automatically, the interesting idea was to try to reproduce it manually and try to get access to Internet.
In order to do that I had to capture data traffic from wireless network and identify IP addresses of other hosts (laptops) that are currently active on the networks. One of the best tools that could help is a network protocol analyzer called Ethereal (
www.ethereal.com). Ethereal is free and provides advanced methods of analysing packets captured from LAN, Wireless or other networks. Yet, to be able to capture packets from the network, WinPcap (
www.winpcap.org) must be installed on our system – it may also come in the package together with Ethereal. In our tests we used Ethereal version 0.10.6 (there is already a newer version available).
I ran the Ethereal, configured it to capture packets from the wireless interface (Capture -> Interfaces) [Figure 2], configured interface to show packets in real-time [Figure 3] and started to capture the packets – the screenshot provided here is just a sample, so on your PC the interface will most likely be different.
Figure 2: Chose Wireless interface to capture packets.
Figure 3: Prepare packets configuration to update in real-time.
After few minutes of collecting packets from the wireless network I had a list of other wireless clients that could use the service as well as data transmitted through the wireless network I was using. While I was capturing the data from the network, my friend was again using the hotspot Internet access to browse web-sites.
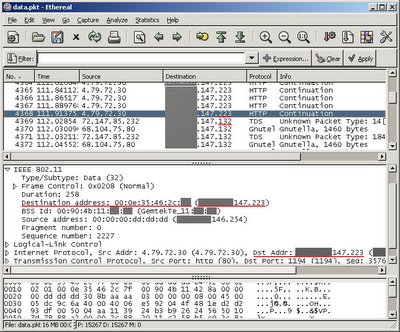
Figure 4: Identify IP address and MAC address of other clients on the network.
Base on the data traffic I specified five different wireless clients on the wireless network, including my and my friend’s laptop that I identified by MAC address (unique 6 bytes identifier of each network card) of his wireless card. The screenshot above [Figure 4] shows two different clients on the network. One with IP ending *.*.147.223 and the other with IP ending *.*.147.132 (Note: The full IP address was hidden in presented screenshots to protect identity of the insecure ISP and save them embarrassment). Base on the MAC address (in the screenshot "Destination address 00:0e:35:46:2c:**") I identified IP address of my friend’s laptop (Dst Addr: *.*.147.223 under Internet Protocol).
Knowing his IP address from the data traffic I manually changed the IP address of my wireless network interface [Figure 5] to the one set on my friend’s laptop (*.*.147.223). After the change familiar message box [Figure 1] appeared indicating IP conflict between our laptops.
 Figure 5: Manually configured IP address of the network interface.
Figure 5: Manually configured IP address of the network interface.
I didn’t even need his username and password to get Internet connection, only his IP address captured from the wireless traffic.
Thus, to access Internet through wireless hotspot without paying, we simply need to change IP address of our wireless interface to IP address of any user who is already logged-in to the hotspot ISP. Obvious conclusion was that this simple technique could be easily repeated by malicious hackers who want to use Jakarta’s commercial wireless Internet hotspot for “free”. It is also important to notice that the
unaware hotspot customers will pay for that connection. Or, if they are aware, the answer of ISP is always the same “Our networks are secure”. Yes, yes … we see that indeed.
Another ISP
The ISP providing hotspot service we tested before is known for ignoring basic security measures and leaving their customers vulnerable to all sorts of hackers. Anyway, this type of attitude is fairly common in Jakarta, as many major companies leave their networks completely insecure and simply don’t care for privacy of their customers. Just out of curiosity we wanted to see if other commercial hotspots around are as much vulnerable as the one we tested, or simply this single ISP company is just so ignorant about security.
First we discovered two other hotspots at the location, connected to one and try to connect to
www.google.com. As expected a login page appeared and we had to type username and password to access the Internet. The hotspot reconnecting technique didn’t work, so I continued analysis with capturing packets using Ethereal (method described earlier in this text).
Using previously described method, I browsed through data capture from wireless traffic and base on information provided in Ethereal I noted the IP addresses (Dst Addr: * under Internet Protocol in Ethereal) and MAC addresses (Destination address under IEEE 802.11 in Ethereal) of clients on the network – refer to previous screenshot [Figure 4].
In the next step I changed my IP address to the IP address of other clients on the network, which generated familiar IP address conflict warning message. Next, I tried to connect to
www.google.com and unfortunately the connection was forbidden. It looked like this ISP already anticipated such threat and
hotspot verifies not only the IP address but also the MAC address, which should be unique for each wireless card. Sounds secure, but is it really secure?
In fact this so called security measure can be pretty weak. It is mostly due to the simple fact that any user connected to wireless network by capturing data traffic can capture the IP address of other wireless clients as well as
MAC address of their wireless cards - that often include users who are already permitted to access the Internet. And as what may surprise some of you, MAC address of wireless card can also be changed. Thus, we can change MAC address of our wireless card to MAC address of other user on the network that is already permitted by the hotspot to access the Internet. In this way we bypass connection filters on hotspots and gain access to Internet.
So, how to change MAC address of wireless card under Windows XP? The simplest method of changing wireless card MAC address under windows is using small application called Macshift - can be downloaded from
here. This little application provides very comfortable way of changing the MAC address of wireless or LAN card under Windows XP.
Using this tool, we can for instance change our Wireless interface named “Wireless Network Connection” [Figure 6].
 Figure 6: Sample Wireless Interface under Windows XP.
Figure 6: Sample Wireless Interface under Windows XP.
But first before we change it, let’s first check the current MAC address of our wireless interface. To see the current MAC address we can run the following command from command prompt:
The sample result of this command is presented below:
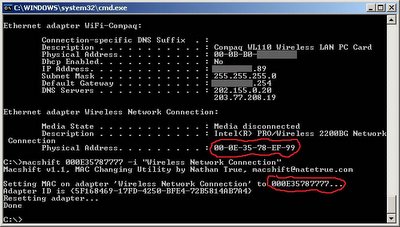
Figure 7: MAC address.
In the result of ipconfig command we can see several network interfaces available. There are two wireless interfaces WiFi-Compaq and Wireless Network Connection and one LAN interface that is not visible in the above screenshot. For the purpose of the test I use the Wireless Network Connection interface, which as we can see currently have MAC address 00-0E-3F-78-EF-99 assigned
In order to change the MAC address of this interface I had to use macshift. Following command syntax applies:
| C:\> macshift NEW_MAC_ADDRESS -i "Interface Name"
|
Accordingly, to change MAC address of our Wireless Network Connection interface to 00-0E-35-78-77-77, I had to execute the following command:
|
C:\> macshift 000E35787777 -i "Wireless Network Connection"
|
The result of the command execution is visible on the screenshot above [Figure 7]. Macshift changed the old MAC address 00-0E-35-78-EF-99 to a new MAC address 00-0E-35-78-77-77 and restarted the interface. This change is not permanent and will be only active until next restart of your Windows XP.
At this point all other devices on the wireless network will see our network card with this MAC address. If previously there was already another wireless card with the same MAC address connected to the network, we will certainly conflict with this card. The effect may be quite unpredictable, usually our connection will be bit unstable until one card disconnects.
However, if this card with the MAC address we are using previously had access to the Internet through hotspot we should be able to access the Internet as well, despite the filter.
Just as predicted, the another hotspot of a different ISP we tested was vulnerable to this attack and again, if someone decide to use this technique to gain access to the Internet, client currently using the hotspot service will most likely pay for it.
Cleary, the security of commercial hotspots in Jakarta is very weak and
the worst issue is that customers of these hotspots can easily become a victims of malicious hackers.
In a very brief summary, the following method can be used by malicious hackers to access the Internet through commercial hotspots without paying:
- Changing the IP address of your wireless card to the IP address used by laptop of a user authenticated to the hotspot,
- Optionally if necessary, changing the IP address and the MAC address of our wireless interface to the IP address and the MAC address of wireless interface used by laptop of a user authenticated to the hotspot.
There are certainly many other hotspot vulnerabilities that could be used to access the Internet without paying. I’ll probably present it after the ISPs fix this current vulnerabilities, which I believe will take months.
Conclusion
Considering the fact, that vast majority of wireless hotspots in Jakarta seriously lack security, I would seriously advise to consider use of this service for anything more than reading Internet news – unless you perfectly understand use of SSL encryption or encrypted tunnelling through SSL/SSH.
Clearly, majority of ISPs in Jakarta are ignorant about security and leave their customers vulnerable to attacks of a malicious hackers. If you use such service face the fact that your Wireless connection is insecure and not encrypted, thus any user with a wireless card can capture information you wirelessly send and receive! This may include your passwords, your e-mails and other sensitive information that might be pretty useful for hackers. Also, it’s important to notice the problem is not in the wireless technology but in the poor implementation.
As for the
legal aspect of running insecure hot-spot service, you may find more in the
following article.
Credits:
- Great Indonesian Arabica coffee producers, brewers etc. – keep up the good work guys allowing me to work late nights,
- Authors of Ethereal,
- Nathan True - author of Macshift,
- Authors of WinPcap library,
- All the Jakarta ISPs that don’t consider safety of their customers as something anyhow important.
Disclaimer:
Information presented here intends to make consumers of commercial wireless hotspots aware of the potential problems related to the use of such service and which internet service provides don’t inform about. Do not try to use techniques described here on real commercial hotspots as it “may” be considered as illegal - hence lack of Cyber law in Indonesia. Any use of techniques described here is at your own risk!


9 comments:
Crazy stuf!!! I can not believe hotspots can be so easily hacked. Did you try this in Singapore?
Piggyjacking rules!
I wonder if the ISPs have any knowledge of what happens. If they do, don't you think they have to do something? What are the rules?
Chrisma, base on your experience of working with ISP I think you must be familiar with implication of telecommunication and customer protection laws in Indonesia. Well, to answer your question fully I asked legal opinion of best lawyers in Jakarta in both fields. I'll post their opinion on my blog before Monday. The initial input from lawyers is very interesting and it seems that some of the ISPs offering such insecure Wi-Fi services may face serious legal implications.
nice post!
are mac users are affected as well? is the wifi devices in those hot spots support IPv6? it's much more difficult to hack if IPv6 is implemented, isn't?
hanindyo at gmail dot com
Just successfully do it.
Have 30 minutes of free access :-D
The problem is strongly related to the network layer, thus all OS are affected.
You are right Hanindyo, IPv6 is more secure and could improve the security, yet it is not supported on local hotspots. The reason is probably that not many users in fact have enabled support for this protocol.
It's not free. By using the technique described in my post you tap (hijack) onto someones connection and this person will pay for that. It's not nice, right? However, there are some other techniques of using local hotspots for free that does not cause financial loss to the users, only to ISPs I guess. As a tip I'll say that it has something to do with open proxy servers (on port 3128) on the ISP network that you can connect to from the hotspot network without restrictions. If you got access to proxy you got access to web.
PS: At Plaza Semangi you got free Wi-Fi access, yet one day it's working another day not, depends on our luck hehe.
hmm.. packet sniffing on hotspot seems more dangerous now.. where we can easily log packets into a file.
i'm using macosx. then tried to capture packets using tcpdump on hotspot cafe for an hour.
i found about 30 plain passwords (including my own pass) on my log. this is so scary..
ISPs / hotspot providers should warn their customers.
IT experts may use the SSL tunneling to avoid this crap. however, how about common-users?
Post a Comment